Currently, one of the hot topics in the digital world has Wannacry Ransomware. This name had been spreading like wild fire, and the reason for it was that ransomware had been the most pervasive cyber threat since 2005. Interestingly, the first ransomware in history emerged in 1989 (that’s 27 years ago) by the name ‘AIDS Trojan.’
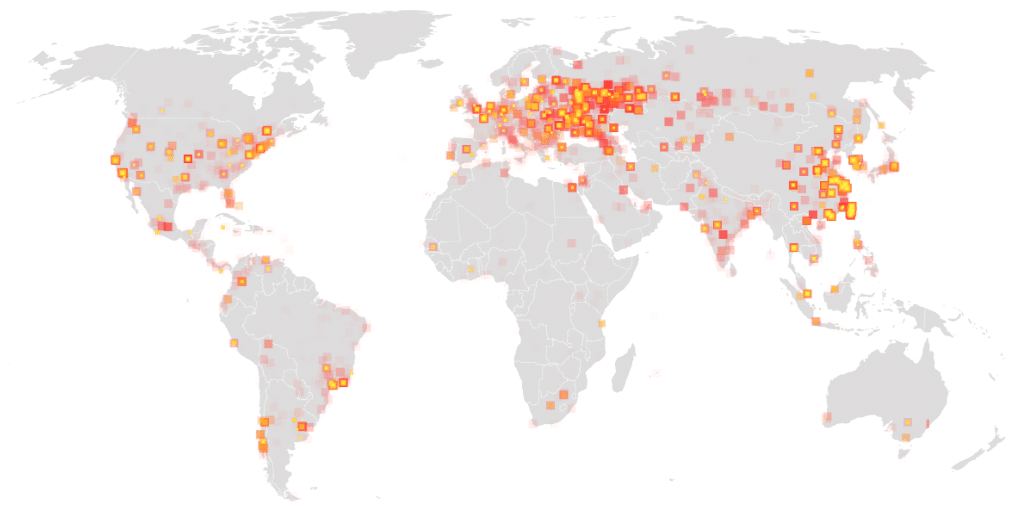
The massive wannacry attack which shook the digital world started on 12 May 2017. Within the first few hours, over a mind-boggling 200,000 machines were infected.
Using this malware, the attackers targeted old windows servers leading to huge business loss and stand still all around the world. Although the fuzz has settled down a bit, this nightmare still haunts vulnerable windows systems.
How Ransomware Infection Happens
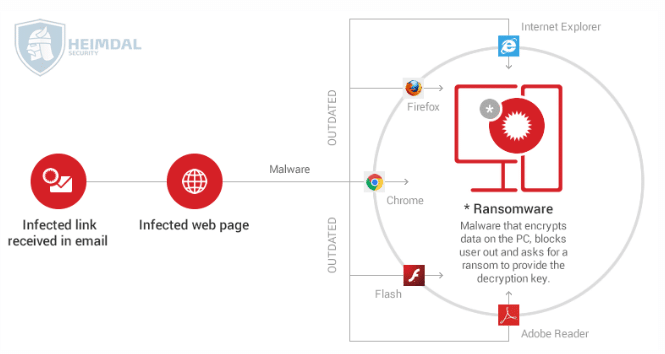
- Initially, the victim receives an email which includes a malware-laden attachment or a malicious link. Alternatively, the virus can originate from a malicious website that delivers a security exploit to create a backdoor on the victim’s PC by using a vulnerable software from the system.
- An attempt by the victim to clicks on the downloads or link and opens the attachment(s), a downloader (payload) will be launched on the affected PC.
- The downloader uses command and control servers controlled by cyber criminals or a list of domains to download the ransomware program on the system.
- The contacted command and control server gives feedback by sending back the asked for data.
- The malware then encrypts the entire hard disk content, personal files, and critical data. Anything and everything, including data stored in cloud accounts (Google Drive, Dropbox) synced on the PC. Data can also be encrypted on other computers connected to the same network.
- An alarm shows on display with the commands on how to pay for the decryption key.
What is Wannacry Ransomware?
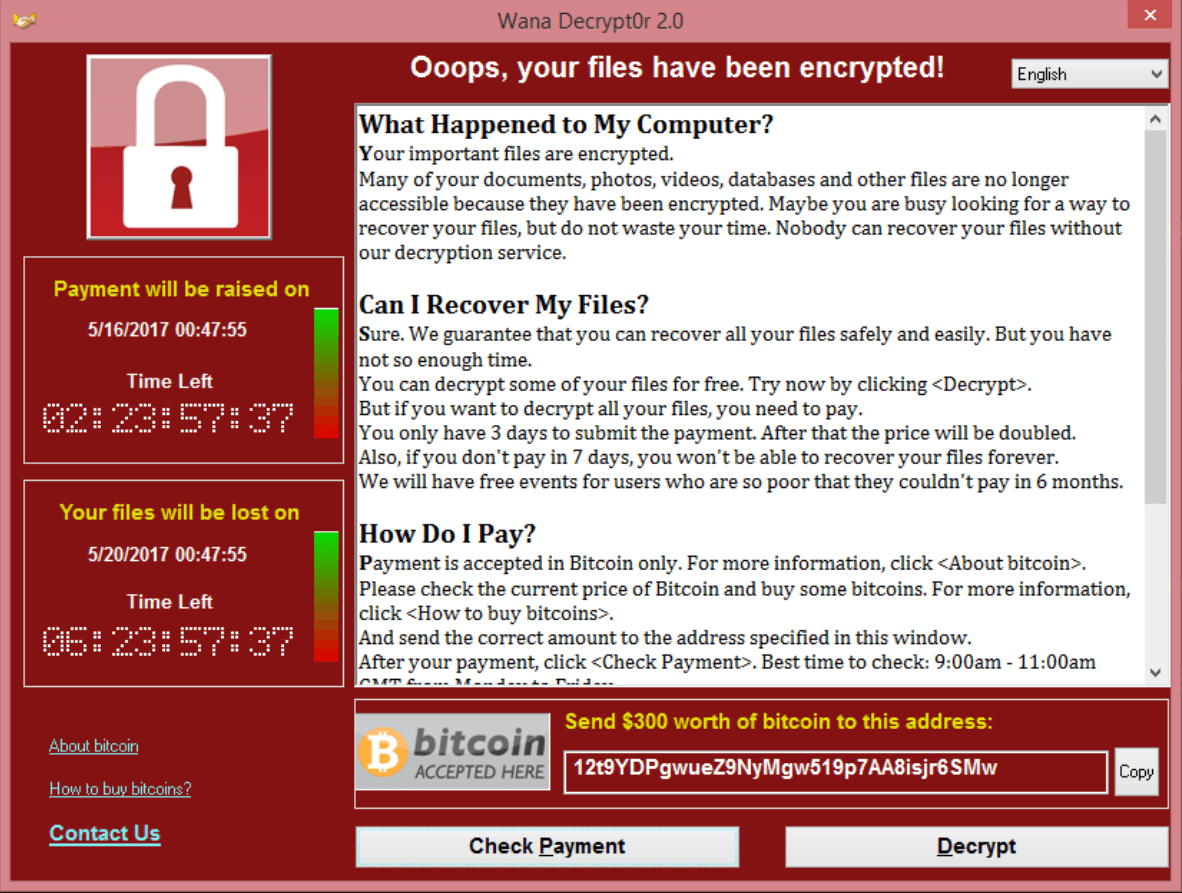
Ransomware is a malware that is designed to encrypt all the data in the victim computer also blocking normal access to the victim system. After information is encrypted, ransomware will demand bitcoins or payment to decrypt the data. The affected machine will show a Popup window on the desktop (count down screen) as below.
Things you need to know about The WannaCry ransomware attack
- A ransomware attack of “unprecedented level” (Europol) started spreading WannaCry ransomware around the world on the Friday of May 12th, ‘17, around 1100 hrs ET/3PM GMT.
- Until now, hundreds of thousands of Windows-running machines in 99 nations have been hit, with the highest numbers of viruses in India, Ukraine, Russia, and Taiwan.
- Cyber criminals are using the EternalBlue exploit released by The Shadow Brokers on 14th of April 2017. This exploit was patched a month before that when Microsoft issued a critical security update (Microsoft Security Bulletin MS17-010).
- The reason why this campaign became so extensive is that it exploits a vulnerability in Windows SMBv1 and SMBv2 to move laterally within networks and infect other computers.
- You are running a vulnerable system if you haven’t installed updates, even though your data hasn’t been encrypted, your PC might still have a backdoor that attackers can leverage in a potential second round attacks.
How it influences?
Ransomware is fundamentally intended to encode every one of the information in windows machines/servers. As per the US Computer Emergency Readiness Team (USCRT), under the Department of Homeland Security, ransomware spreads effectively when it experiences unpatched or obsolete programming. These culprits go for the most straightforward approach to taint a framework or system and utilize that secondary passage to spread the vindictive substance. Specialists trust that WannaCry is transmitted by a web worm (an independent malware PC program) that repeats itself by hacking into different PCs associated with a system, as opposed to the standard instance of provoking clueless clients to open connections (email attachment documents). It is additionally trusted that the digital assault was done with the assistance of instruments stolen from the National Security Agency (NSA) of the United States.
Wannacry ransomware is the name for a productive hacking assault known as “ransomware,” that holds your PC prisoner until the point when you pay. When it taints a PC, it encodes – or essentially scrambles – every one of the information, that is the way it works. At that point, the framework sets up a screen requesting that you pay a payment before your data can be unscrambled. Ordinarily, the cost increments after some time until the finish of the counter, when the records are obliterated.
Aside from being the biggest ransomware assault since time started, there are a couple of different reasons why this attack is especially extraordinary. While the strategies that were utilized were not new on the web, the approach was – that is, programmers took two of the most astute courses in which to target associations and consolidated them to build up an overall cyber security circumstance.
All signs point to the underlying disease happening through a common phishing endeavour, in which clueless laborers downloaded tainted records in their email. The thing that made WannaCry so impactful was its ability to split far from its underlying PC and quickly spread the system, contaminating PCs on a system afterward.
When phishing is occurring, a fast-moving worm and ransomware are not in themselves one of a kind, the blend of this arrangement was lamentable. Since WannaCry needn’t bother with any collaboration going concerning the criminal, it was the ideal strategy to rapidly crossing all through a dangerous endeavour.
While this approach isn’t entirely new, it is disturbing and has all the earmarks of being the first occasion when that a ransomware payload has been focused along these lines at such an extensive scale.
Ransomware is not another issue. It has been around for quite a long time, and it’s been discussed vigorously in the security business for a long while. Be that as it may, it keeps on being one of the best reasons for worry for CISOs, and ransomware assaults grew 36% of every 2016. So why is it proceeding to have such a remarkable effect on cyber security? Since illuminating this test is a hard nut to pop open.
Ransomware appears to be prevailing because of its dependence on the human component, and as much as we prefer not to let it be known, people are on a fundamental level to be faulted. This is the reason WannaCry kept on influencing PC actually into the week following the past assault, in spite of numerous associations spending all end of the week informing people in general and their managers and settling the issue that hit amid a working day on a Friday. It doesn’t make a difference how much worker preparing or mindfulness goes into training your representatives or the general population to forgo erasing cryptic messages, opening connections and focusing on the important indications of ransomware, the minor dependence on people is a fundamental issue that isn’t possible away with.
All in all, what can you do to cover your association from an excellent focusing on? While ransomware targets and assaults may have built up, the approaches to secure yourself have not. There are a couple of steps that associations ought to completely investigate to be in the sheltered zone.
In the wake of turning into the victims, an ideal approach to react to a ransomware assault is to wipe your frameworks, evacuating the programmers’ ability to control your data. Never consult with assailants. Apparently, that wipes out all your particular information, which implies it’s essential to have great back-ups, accordingly evacuating the control that hoodlums have over your information and yourself. Understanding your Association’s utilization and distribution center of data, and going down all that data, is a key initial move toward keeping any implications of a future ransomware assault.
It’s likewise imperative to think of an arrangement of activity if your association is attacked. Consider the potential ramifications to your remaining in the market, for example, organization valuation or open brand perspective, on the off chance that you do or don’t pay the sum inquired. Has an arrangement set up that recognizes the distinctive partners that should be informed before you go to your choice, so you are completely mindful of the levels of leadership to rapidly and quickly execute a remediation design if it’s vital?
On the off chance that there is anything WannaCry episode showed us, it’s that worldwide, across the board ransomware can and will affect associations with no notice.
WannaCry was first heard in the UK’s well-being administration, which had all the earmarks of being one of the greatest PC frameworks to be contaminated. It’s likewise called WannaCrypt.
How to know if your system is patched
If you’re unsure whether your computer is updated to the latest version, you can run Microsoft Baseline Security Analyzer 2.3 and discover which the missing updates. The tool also lists the unavailable updates by severity and the likely effect.
It will be ideal if you realize that you can just utilize this device on one PC or a gathering of PCs. On the off chance that you need to cover your whole foundation, you should use your interior IPs and facilitate your updates
Software that has adopted similar strategies:
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2012 R2
- Microsoft Windows XP
- Microsoft Windows RT 8.1
- Microsoft Windows Server 2003
- Microsoft Windows 7
- Microsoft Windows 8.1
- Microsoft Windows 10
- Microsoft Windows Server 2016
Common infecting ways used by cyber criminals
- Spam email that carries malicious attachments or links
- Some add-ons or plugin on web browsers
- SMS messages (when targeting mobile devices)
- Security exploits in vulnerable software
- Legitimate websites that have malicious code injected in their web pages
- Internet traffic redirects to malicious websites
- Botnets
- Self-propagation (distribution from one infected computer to another)
How can we prevent ransomware attacks?
Microsoft has given the security patches for all known Operating System versions, and any needed security patch should be used to your Windows servers.
Locally, on the PC
- Disable the outdated SMBv1 protocol and block incoming traffic in SMB port 445. The ransomware spreads across a network using a vulnerability in servers SMB. The SMB (Server Message Block) is a network file sharing protocol used to transfer files. Due to the security vulnerabilities in the windows server, it’s a primary key for the hackers to break the server easily. The exploit used goes by the name ‘ETERNALBLUE’ which is believed to be created by the National Security Agency (NSA) of the U.S. It was leaked by the ‘Shadow Brokers’ hacker group on April 14, 2017. This vulnerability was fixed in MS17-010 released in March.
- Backup all your files and data frequently. Ideally, you should make at least three copies of your backup data on two medias that are different. One backup copy must be offline all the time. Although this is a bit difficult task, there is no other better option to save data.
- Scan the server for WANNACRY ransomware hashes in files and remove the ones that are affected. (Remove all the files with extensions .WANNACRY)
- Patch your system including device drivers and BIOS
- Do not use outdated and unsupported software
- Turn on firewall on both your router and computer
- Avoid using pirated software
- If the server is infected, immediately disable the SMB port and try to retrieve the files. There are a few online tools available to decrypt data. However, these do not work for all encrypted file.
- Secure the server data and network to protect it from hackers and regularly audit the servers and network for any vulnerabilities.
- Setting up mailchannels: Mail servers should be secured, and all outgoing and incoming emails should be scanned for malicious attachments or viruses. Setup email filters to block spamming and spoofing.
- Make sure that anti-virus programs are installed and up to date. It is beneficial to monitor the malware.
- Securing the server using firewalls and disabling unwanted ports and protocols.
- Don’t store critical data only on your PC.
- You ought to have two backups of your data: on an external hard drive and in the cloud – Dropbox/Google Drive/OneDrive, etc.
- Make sure the Dropbox/Google Drive/OneDrive/etc. application on your computer is not turned on by default. To sync your data, you only open them once a day and close them once this is done.
- Your software and OS you use should be up to date, including the latest security updates.
What you can (and should) do right now
- Check if your system is patched. (See above.)
- Download and install all system updates and restart your PC to apply them.
- Make sure you have a proactive safety layer in place. (Maybe you’d even like to see what Heiman PRO can do.)
- Ensure that you have a (paid) antivirus solution and that it’s up to date.
- Back up your data in at least two places, if you haven’t done it already.
- Ensure that you use all software updates, the moment they are made available.
- Teach yourself to detect and keep off phishing emails and links.
It may likewise be used to experience this hostile to ransomware agenda (printable form) and perceive how you’re doing and what else you could do to guard your information from WannaCry and different strains. What’s more, in case you need to plunge further into the subject, here are two specific investigations that you may discover accommodating: from Talos Intelligence and Malwarebytes. Keep in mind; digital security is not just about the huge occasions that happen and stands out as truly newsworthy. Essential parts of it are the manner by which you handle yourself online consistently, how you shape your digital cleanliness propensities.
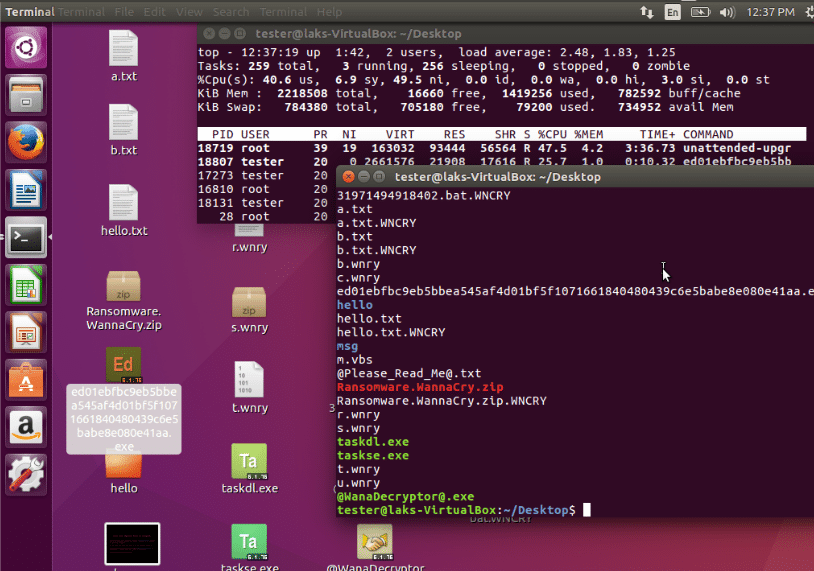
How Ransomware effect Linux based systems are running Wine
Wine is a windows compatibility layer, which makes it possible for Linux users to run a windows.EXE file.
Wannacry also affects the windows files and directories which are configured under wine. However, it does not change the root (/) directory or other user owned-files on the machine. It mainly encrypts the windows files only.
Conclusion
Ransomware conveyed coercion to a worldwide scale, and it’s up to every one of end-users, entrepreneurs, and chiefs, to disturb it. It’s being realized now that, creating malware or ransomware dangers is presently a business and it ought to be dealt with, all things considered. The exhibit risk scene is ruled by all around characterized and all around supported gatherings that utilize propelled specialized instruments and social designing aptitudes to get to PC frameworks and systems; even more, digital criminal collections are procured by expensive states to target financial goals, as well as political and fundamental interests. It was also realized that it is not frail and there’s a modest bunch of basic things that can be done to stay away from ransomware. Remain safe and remember the best assurance is dependably a reinforcement!
STILL SPENDING TIME ON SUPPORT?
Outsource your helpdesk support to save time and money. We have technicians available for little over 5 USD per hour in order to assist your customers with their technical questions. Grow your business and concentrate more on your SALES!
Xieles Support is a provider of reliable and affordable internet services, consisting of Outsourced 24×7 Technical Support, Remote Server Administration, Server Security, Linux Server Management, Windows Server Management and Helpdesk Management to Web Hosting companies, Data centers and ISPs around the world. We are experts in Linux and Windows Server Administration, Advanced Server Security, Server Security Hardening. Our primary focus is on absolute client satisfaction through sustainable pricing, proactively managed services, investment in hosting infrastructure and renowned customer support.