Securing your Kubernetes cluster with eBPF (extended Berkeley Packet Filter) is a powerful approach to strengthen the overall security of your environment. This kernel tool allows users to programmatically extend kernel capabilities without changing the kernel source code. eBPF is a small kernel tool that can run micro mini programs inside the N-hooks of kernels. So, in the live kernel itself, you can add multiple functionalities like getting the traces of an application enforcing Securities and then changing the network traffic. eBPF technology allows you to attach custom programs to various kernel events, providing enhanced observability and control over network packets. By leveraging eBPF in your Kubernetes cluster, you can implement advanced security with eBPF to protect your applications and data.
Use cases of eBPF
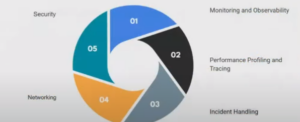
- Network Tracing and Monitoring: eBPF allows for efficient packet filtering, making it ideal for tracing and monitoring networks. It can capture and analyze network packets in real time, providing insights into network behavior and performance.
- Security and Intrusion Detection: eBPF enables the creation of custom security policies and intrusion detection mechanisms within the kernel. It can monitor and filter network activities, helping to detect and prevent security threats.
- Performance Analysis: eBPF can be used for profiling and performance analysis of kernel and user-space applications. It provides a non-intrusive way to gather detailed performance metrics, aiding optimization efforts.
- Dynamic Tracing of Applications: With tools like BPFtrace, eBPF allows developers and administrators to trace system and application events. This aids in debugging, understanding system behavior, and identifying performance bottlenecks.
- Custom Load Balancing: eBPF can be employed to implement custom load balancing logic within the kernel. You can use custom load balancing when load-balancing requirements are not met by standard networking solutions.
- Container Orchestration: eBPF is used by container environments, including orchestration platforms like Kubernetes. It provides enhanced network visibility, security, and performance monitoring for containerized workloads.
- Distributed Systems Observability: Distributed systems gather insights into the communication and interactions between various components using eBPF. This is valuable for troubleshooting and optimizing the performance of complex, distributed applications.
- Custom Firewalling: eBPF allows the creation of custom firewall rules directly within the kernel. This capability provides a flexible and efficient way to filter network traffic based on specific criteria.
- Filesystem Monitoring: eBPF can monitor filesystem activities, such as file opens, reads, and writes. This is beneficial for auditing and understanding how applications interact with the filesystem.
- Real-time Telemetry:eBPF enables the collection of real-time telemetry data from various system parts. This data can be used for monitoring, alerting, and making informed decisions about system behavior.
- eBPF’s flexibility and performance make it a valuable tool for a wide range of use cases, especially in the networking context, security, and observability in modern computing environments.
Use cases of eBPF in Kubernetes
Using eBPF in Kubernetes offers several advantages, enhancing observability, security, and performance management within containerized environments. Here are some key reasons to use eBPF in Kubernetes:
- Enhanced Networking Visibility: eBPF enables detailed packet-level visibility into network interactions between containers and provides insights into communication patterns and potential issues. This is crucial for troubleshooting and optimizing network performance in Kubernetes clusters.
- Dynamic Tracing and Monitoring: With eBPF, you can dynamically trace and monitor system calls, application events, and kernel activities in real time. This is valuable for debugging, performance analysis, and understanding the behavior of applications running in Kubernetes.
- Efficient Security Policies: eBPF allows the creation of custom security policies within the kernel, enabling more granular and efficient network traffic filtering. This is beneficial for implementing security controls and intrusion detection mechanisms in Kubernetes environments.
- Container-level Observability: eBPF can be used to gather detailed telemetry data at the container level, offering insights into resource utilization, application behavior, and performance metrics. This enhances observability for both developers and operators.
- Custom Load Balancing Logic: In Kubernetes, eBPF can implement custom load-balancing logic directly in the kernel. This provides a flexible and efficient way to distribute network traffic across services or pods based on specific requirements.
- Reduced Overhead and Latency: eBPF programs run within the kernel space, reducing the overhead associated with traditional user-space monitoring tools. This results in lower latency and improved overall system performance.
- Security and Compliance: eBPF can assist in implementing custom security checks and compliance controls directly within the kernel. This is especially important in environments where strict security measures and compliance standards are to be adhered to.
- Dynamic Ingress and Egress Control: Using eBPF, you can dynamically control and filter both incoming and outgoing network traffic for containers. This fine-grained control is beneficial for enforcing network policies and access controls in Kubernetes clusters.
- Improved Resource Utilization: eBPF facilitates efficient resource monitoring and optimization by providing detailed insights into how resources are utilized at the kernel level. This can help in identifying and addressing performance bottlenecks.
- Compatibility with Container Runtimes: eBPF is compatible with various container runtimes, including Docker and Containers, making it suitable for a wide range of Kubernetes deployments.
eBPF brings powerful networking, security, and observability to Kubernetes, offering a more efficient and flexible approach to managing and monitoring containerized workloads.
Vulnerabilities in container technology
Container technology, including the use of eBPF, has gained popularity for its flexibility and efficiency. Like any technology, we should be aware of potential vulnerabilities and security considerations. Here are some aspects to consider regarding the vulnerability of container technology with eBPF:
Kernel-Level Access: eBPF programs run in the kernel space and vulnerabilities in eBPF code or misconfigurations could potentially lead to kernel-level exploits. It’s crucial to ensure the security and integrity of eBPF programs to prevent unauthorized access or manipulation.
Network Exploitation: Since eBPF is commonly used for networking tasks, vulnerabilities in eBPF networking programs could be exploited for malicious purposes, leading to network-based attacks within containerized environments.
Container Runtime Security: The security of container runtimes (e.g., Docker, containers) is integral to overall container security. Vulnerabilities in container runtimes may indirectly impact the security of eBPF programs running within containers.
Shared Kernel Space: Containers share the same kernel with the host and other containers. Any vulnerabilities in the kernel or eBPF programs could potentially impact the security isolation between containers.
For mitigating these vulnerabilities, it’s essential to follow security best practices, stay informed about security updates, conduct regular security audits, and implement defense-in-depth strategies to enhance the overall security posture of containerized environments using eBPF.
Conclusion
Securing your Kubernetes cluster with eBPF requires knowledge and expertise in kernel programming and security best practices. It is crucial to carefully design and validate your eBPF programs to ensure they don’t impact performance or stability. Regular security audits and updates to eBPF programs are essential to keep up with emerging threats and vulnerabilities. Leveraging eBPF in your Kubernetes cluster provides a powerful toolset for enhancing security, visibility, and control, enabling you to proactively protect applications and data from potential threats.
Metclouds Technologies’ team of experts helps to enhance your Kubernetes cluster security by implementing eBPF measures.







