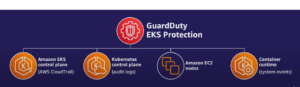
As organizations increasingly adopt container orchestration systems like Kubernetes for deploying and managing containerized applications, ensuring the security of these environments becomes paramount. Amazon GuardDuty, a managed threat detection service by AWS, plays a crucial role in enhancing the security posture of AWS accounts. When combined with Amazon Elastic Kubernetes Service (EKS), GuardDuty can provide comprehensive runtime monitoring for Kubernetes clusters. Amazon GuardDuty runtime monitoring adds visibility to individual Kubernetes container runtime activities such as file access, process execution, and network connections. Continuously monitors all Amazon EKS clusters across your organization. Provides over two dozen new threat detections leveraging high-fidelity system-level events tailored for known container attack techniques and providing container-level context. Amazon GuardDuty runtime monitoring detects threats at each layer of Kubernetes deployment on Amazon EKS.
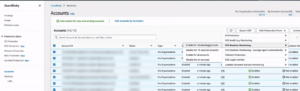
To enable GuardDuty runtime monitoring, you need an IM role with appropriate permissions to manage GuardDuty for your accounts—log into your GuardDuty delegated administrator account. Go to the GuardDuty console. Navigate to the left panel and click Accounts. Here, you can see all the members’ accounts in your earliest organization and the status of GuardDuty for each account. Also, you can see whether the specific features are enabled or disabled for each account. This time, EKS Runtime Monitoring is disabled.
How to enable EKS Runtime Monitoring
Enabling EKS Runtime Monitoring is a two-step process.
- Select the accounts you want to enable and click the Edit Protection Plan button. Select EKS Runtime Monitoring and Enable for selected accounts. Then click on Confirm.
2. Select how you want to manage the agent. GuardDuty integrates with EKS to manage the agent on your behalf across your EKS clusters. If you select this option, the lifecycle of the agent is managed by the GuardDuty including updates to the agent. GuardDuty also creates a VPC endpoint for the agent to communicate with the GuardDuty service. To use this option, select the accounts where you want to manage the agent automatically and click the Edit Protection Plan button. Select EKS Runtime Monitoring – manage agent automatically and Enable for selected accounts. Then click on Confirm.
How to monitor the coverage using GuardDuty
Step 1. Go to the EKS Protection page and select EKS clusters runtime coverage.
Here, you can see the monitoring status of all EKS clusters in your organization. A status Unhealthy indicates GuardDuty is not able to monitor this cluster. The issue column shows the reason.
Step 2. Go to the Findings page and sort the EKS cluster findings using the Resource type filter.
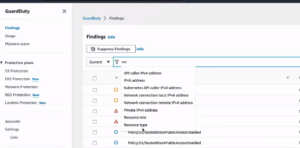
Here, you can see all findings where the effective resource is an EKS cluster. Findings identified using the runtime monitoring are visible here.
For example, the runtime NewLibraryLoaded is a finding generated by EKS runtime monitoring. It tells the process in the container loaded a new library. It is a best practice for containers to be immutable and binary files, scripts, or libraries should not be modified during their lifetime. A new library loaded can be potentially malicious. GuardDuty also provides the lineage to identify the caller process that can help with analysis and forensics investigation of the culprit processes.
Conclusion
Amazon GuardDuty runtime monitoring brings advanced threat detection and container orchestration, offering organizations a robust solution for securing their containerized applications in the cloud. Regularly reviewing GuardDuty findings and implementing security best practices within EKS ensures a resilient and secure Kubernetes environment on AWS.
Xieles support is here to protect your Kubernetes with Amazon GuardDuty







